Decrypt Cisco Secret 4
Cain Abel Download. Important note Some antivirus and antispyware programs flag Cain Abel as being infectedmalware, although the application is perfectly safe and does not pose a threat to your system. This is called a false positive. The term false positive is used when antivirus software wrongly classifies an innocuous inoffensive file as a virus. The incorrect detection may be due to heuristics or to an incorrect virus signature in a database. Similar problems can occur with antitrojan or antispyware software. Cain Abel is a nifty program that deals with recovering lost passwords using the most powerful and tough decryption algorithms. Cisco type 7 password decrypt hack crack. This page allows users to reveal Cisco Type 7 encrypted passwords. Crack Cisco Secret 5 Passwords. Understand the difference. Decrypt Cisco Secret 4' title='Decrypt Cisco Secret 4' />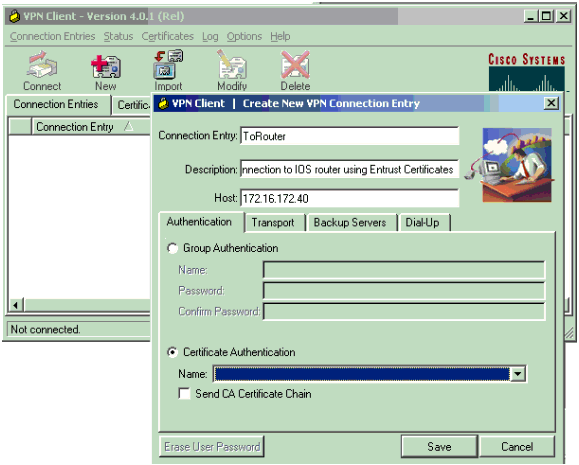 If service passwordencryption is not configured on the Cisco device, simply read the plain text passwords from the configuration file. If service password. This document demonstrates how to configure a connection between a router and the Cisco VPN Client 4. Remote Authentication DialIn User Service RADIUS for. And you have filled out the PreMasterSecret log filename field in your preferences Be aware that Wireshark might be sniffing traffic that is not sent by. Internet Protocol Security IPSec Cisco IOS uses the industrystandard IPSec protocol suite to enable advanced VPN features. The PIX IPSec implementation is based on. It is capable to quickly and efficiently retrieve Outlook and network passwords and to display passwords underneath asterisks. Recovery and prevention components. Note that the application relies on Win. Pcap to be able to scan and reveal info, so you need to make sure its installed, but the general setup package offers to grab it for you to save some time and effort. Most encrypted passwords are breakable using this program via Dictionary, Brute Force and Cryptanalysis attacks. Decrypting scrambled passwords or wireless network keys is not a challenge either. Besides the ability to record Vo. IP conversations, the application also features the possibility to analyze route protocols. Cain Abel is made of two major components the first one, Cain, is the frontend application that recovers passwords and the password sniffing part the second one, Abel, is a Windows NT service that requires to be installed locally or remotely and has the role of scrambling the traffic inside the network, for additional protection. Scan local and network services. The program doesnt seek to impress through looks, which is why the user interface may seem a little unpolished. At a closer look, it sports an organized and easy to explore panel, while the additional menus encompass a wide range of tools. These include a Route Table utility, a Base. Cisco Password Decoder, a hash calculator, a RSA Secur. ID Token Calculator, to name a few. Cain Abels interface is divided into several sections, the first of which deals with decoding passwords for Internet Explorer, Windows Mail, Dialup Passwords, as well as others. Other panels include a Sniffer detects and retains passwords, a Trace Route Utility and a Wireless Scanner identifies wireless networks and provides details on MAC addresses. In conclusion. Bottom line is that you cant go wrong with Cain Abels decoding algorithms. Its witty enough to recover the strongest passwords stored on your computer and features a bunch of other hash and decryption utilities that recommend it. Developing Network Security Strategies Network Security Design. Developing security strategies that can protect all parts of a complicated network while having a limited effect on ease of use and performance is one of the most important and difficult tasks related to network design. Security design is challenged by the complexity and porous nature of modern networks that include public servers for electronic commerce, extranet connections for business partners, and remote access services for users reaching the network from home, customer sites, hotel rooms, Internet cafes, and so on. To help you handle the difficulties inherent in designing network security for complex networks, this chapter teaches a systematic, top down approach that focuses on planning and policy development before the selection of security products. The goal of this chapter is to help you work with your network design customers in the development of effective security strategies, and to help you select the right techniques to implement the strategies. The chapter describes the steps for developing a security strategy and covers some basic security principles. The chapter presents a modular approach to security design that will let you apply layered solutions that protect a network in many ways. The final sections describe methods for securing the components of a typical enterprise network that are most at risk, including Internet connections, remote access networks, network and user services, and wireless networks. Security should be considered during many steps of the top down network design process. This isnt the only chapter that covers security. Chapter 2, Analyzing Technical Goals and Tradeoffs, discussed identifying network assets, analyzing security risks, and developing security requirements. Chapter 5, Designing a Network Topology, covered secure network topologies. This chapter focuses on security strategies and mechanisms. Following a structured set of steps when developing and implementing network security will help you address the varied concerns that play a part in security design. Many security strategies have been developed in a haphazard way and have failed to actually secure assets and to meet a customers primary goals for security. Breaking down the process of security design into the following steps will help you effectively plan and execute a security strategy Identify network assets. Analyze security risks. Analyze security requirements and tradeoffs. Develop a security plan. Define a security policy. Develop procedures for applying security policies. Develop a technical implementation strategy. Achieve buy in from users, managers, and technical staff. Train users, managers, and technical staff. Implement the technical strategy and security procedures. Test the security and update it if any problems are found. Maintain security. Chapter 2 covered steps 1 through 3 in detail. This chapter quickly revisits steps 1 through 3 and also addresses steps 4, 5, 6, and 1. Steps 7 through 1. Chapter 1. 2, Testing Your Network Design, addresses Step 1. Identifying Network Assets. Chapter 2 discussed gathering information on a customers goals for network security. As discussed in Chapter 2, analyzing goals involves identifying network assets and the risk that those assets could be sabotaged or inappropriately accessed. It also involves analyzing the consequences of risks. Network assets can include network hosts including the hosts operating systems, applications, and data, internetworking devices such as routers and switches, and network data that traverses the network. Less obvious, but still important, assets include intellectual property, trade secrets, and a companys reputation. Analyzing Security Risks. Risks can range from hostile intruders to untrained users who download Internet applications that have viruses. Hostile intruders can steal data, change data, and cause service to be denied to legitimate users. Denial of service Do. S attacks have become increasingly common in the past few years. See Chapter 2 for more details on risk analysis. Analyzing Security Requirements and Tradeoffs. Chapter 2 covers security requirements analysis in more detail. Although many customers have more specific goals, in general, security requirements boil down to the need to protect the following assets The confidentiality of data, so that only authorized users can view sensitive information. The integrity of data, so that only authorized users can change sensitive information. System and data availability, so that users have uninterrupted access to important computing resources. According to RFC 2. Site Security Handbook One old truism in security is that the cost of protecting yourself against a threat should be less than the cost of recovering if the threat were to strike you. Cost in this context should be remembered to include losses expressed in real currency, reputation, trustworthiness, and other less obvious measures. As is the case with most technical design requirements, achieving security goals means making tradeoffs. Tradeoffs must be made between security goals and goals for affordability, usability, performance, and availability. Also, security adds to the amount of management work because user login IDs, passwords, and audit logs must be maintained. Security also affects network performance. Mac Keygen. Security features such as packet filters and data encryption consume CPU power and memory on hosts, routers, and servers. Encryption can use upward of 1. CPU power on a router or server. Encryption can be implemented on dedicated appliances instead of on shared routers or servers, but there is still an effect on network performance because of the delay that packets experience while they are being encrypted or decrypted. Another tradeoff is that security can reduce network redundancy. If all traffic must go through an encryption device, for example, the device becomes a single point of failure. This makes it hard to meet availability goals. Security can also make it harder to offer load balancing. Some security mechanisms require traffic to always take the same path so that security mechanisms can be applied uniformly. For example, a mechanism that randomizes TCP sequence numbers so that hackers cant guess the numbers wont work if some TCP segments for a session take a path that bypasses the randomizing function due to load balancing. Developing a Security Plan. One of the first steps in security design is developing a security plan. A security plan is a high level document that proposes what an organization is going to do to meet security requirements. The plan specifies the time, people, and other resources that will be required to develop a security policy and achieve technical implementation of the policy. As the network designer, you can help your customer develop a plan that is practical and pertinent. The plan should be based on the customers goals and the analysis of network assets and risks. A security plan should reference the network topology and include a list of network services that will be provided for example, FTP, web, email, and so on. This list should specify who provides the services, who has access to the services, how access is provided, and who administers the services. As the network designer, you can help the customer evaluate which services are definitely needed, based on the customers business and technical goals.
If service passwordencryption is not configured on the Cisco device, simply read the plain text passwords from the configuration file. If service password. This document demonstrates how to configure a connection between a router and the Cisco VPN Client 4. Remote Authentication DialIn User Service RADIUS for. And you have filled out the PreMasterSecret log filename field in your preferences Be aware that Wireshark might be sniffing traffic that is not sent by. Internet Protocol Security IPSec Cisco IOS uses the industrystandard IPSec protocol suite to enable advanced VPN features. The PIX IPSec implementation is based on. It is capable to quickly and efficiently retrieve Outlook and network passwords and to display passwords underneath asterisks. Recovery and prevention components. Note that the application relies on Win. Pcap to be able to scan and reveal info, so you need to make sure its installed, but the general setup package offers to grab it for you to save some time and effort. Most encrypted passwords are breakable using this program via Dictionary, Brute Force and Cryptanalysis attacks. Decrypting scrambled passwords or wireless network keys is not a challenge either. Besides the ability to record Vo. IP conversations, the application also features the possibility to analyze route protocols. Cain Abel is made of two major components the first one, Cain, is the frontend application that recovers passwords and the password sniffing part the second one, Abel, is a Windows NT service that requires to be installed locally or remotely and has the role of scrambling the traffic inside the network, for additional protection. Scan local and network services. The program doesnt seek to impress through looks, which is why the user interface may seem a little unpolished. At a closer look, it sports an organized and easy to explore panel, while the additional menus encompass a wide range of tools. These include a Route Table utility, a Base. Cisco Password Decoder, a hash calculator, a RSA Secur. ID Token Calculator, to name a few. Cain Abels interface is divided into several sections, the first of which deals with decoding passwords for Internet Explorer, Windows Mail, Dialup Passwords, as well as others. Other panels include a Sniffer detects and retains passwords, a Trace Route Utility and a Wireless Scanner identifies wireless networks and provides details on MAC addresses. In conclusion. Bottom line is that you cant go wrong with Cain Abels decoding algorithms. Its witty enough to recover the strongest passwords stored on your computer and features a bunch of other hash and decryption utilities that recommend it. Developing Network Security Strategies Network Security Design. Developing security strategies that can protect all parts of a complicated network while having a limited effect on ease of use and performance is one of the most important and difficult tasks related to network design. Security design is challenged by the complexity and porous nature of modern networks that include public servers for electronic commerce, extranet connections for business partners, and remote access services for users reaching the network from home, customer sites, hotel rooms, Internet cafes, and so on. To help you handle the difficulties inherent in designing network security for complex networks, this chapter teaches a systematic, top down approach that focuses on planning and policy development before the selection of security products. The goal of this chapter is to help you work with your network design customers in the development of effective security strategies, and to help you select the right techniques to implement the strategies. The chapter describes the steps for developing a security strategy and covers some basic security principles. The chapter presents a modular approach to security design that will let you apply layered solutions that protect a network in many ways. The final sections describe methods for securing the components of a typical enterprise network that are most at risk, including Internet connections, remote access networks, network and user services, and wireless networks. Security should be considered during many steps of the top down network design process. This isnt the only chapter that covers security. Chapter 2, Analyzing Technical Goals and Tradeoffs, discussed identifying network assets, analyzing security risks, and developing security requirements. Chapter 5, Designing a Network Topology, covered secure network topologies. This chapter focuses on security strategies and mechanisms. Following a structured set of steps when developing and implementing network security will help you address the varied concerns that play a part in security design. Many security strategies have been developed in a haphazard way and have failed to actually secure assets and to meet a customers primary goals for security. Breaking down the process of security design into the following steps will help you effectively plan and execute a security strategy Identify network assets. Analyze security risks. Analyze security requirements and tradeoffs. Develop a security plan. Define a security policy. Develop procedures for applying security policies. Develop a technical implementation strategy. Achieve buy in from users, managers, and technical staff. Train users, managers, and technical staff. Implement the technical strategy and security procedures. Test the security and update it if any problems are found. Maintain security. Chapter 2 covered steps 1 through 3 in detail. This chapter quickly revisits steps 1 through 3 and also addresses steps 4, 5, 6, and 1. Steps 7 through 1. Chapter 1. 2, Testing Your Network Design, addresses Step 1. Identifying Network Assets. Chapter 2 discussed gathering information on a customers goals for network security. As discussed in Chapter 2, analyzing goals involves identifying network assets and the risk that those assets could be sabotaged or inappropriately accessed. It also involves analyzing the consequences of risks. Network assets can include network hosts including the hosts operating systems, applications, and data, internetworking devices such as routers and switches, and network data that traverses the network. Less obvious, but still important, assets include intellectual property, trade secrets, and a companys reputation. Analyzing Security Risks. Risks can range from hostile intruders to untrained users who download Internet applications that have viruses. Hostile intruders can steal data, change data, and cause service to be denied to legitimate users. Denial of service Do. S attacks have become increasingly common in the past few years. See Chapter 2 for more details on risk analysis. Analyzing Security Requirements and Tradeoffs. Chapter 2 covers security requirements analysis in more detail. Although many customers have more specific goals, in general, security requirements boil down to the need to protect the following assets The confidentiality of data, so that only authorized users can view sensitive information. The integrity of data, so that only authorized users can change sensitive information. System and data availability, so that users have uninterrupted access to important computing resources. According to RFC 2. Site Security Handbook One old truism in security is that the cost of protecting yourself against a threat should be less than the cost of recovering if the threat were to strike you. Cost in this context should be remembered to include losses expressed in real currency, reputation, trustworthiness, and other less obvious measures. As is the case with most technical design requirements, achieving security goals means making tradeoffs. Tradeoffs must be made between security goals and goals for affordability, usability, performance, and availability. Also, security adds to the amount of management work because user login IDs, passwords, and audit logs must be maintained. Security also affects network performance. Mac Keygen. Security features such as packet filters and data encryption consume CPU power and memory on hosts, routers, and servers. Encryption can use upward of 1. CPU power on a router or server. Encryption can be implemented on dedicated appliances instead of on shared routers or servers, but there is still an effect on network performance because of the delay that packets experience while they are being encrypted or decrypted. Another tradeoff is that security can reduce network redundancy. If all traffic must go through an encryption device, for example, the device becomes a single point of failure. This makes it hard to meet availability goals. Security can also make it harder to offer load balancing. Some security mechanisms require traffic to always take the same path so that security mechanisms can be applied uniformly. For example, a mechanism that randomizes TCP sequence numbers so that hackers cant guess the numbers wont work if some TCP segments for a session take a path that bypasses the randomizing function due to load balancing. Developing a Security Plan. One of the first steps in security design is developing a security plan. A security plan is a high level document that proposes what an organization is going to do to meet security requirements. The plan specifies the time, people, and other resources that will be required to develop a security policy and achieve technical implementation of the policy. As the network designer, you can help your customer develop a plan that is practical and pertinent. The plan should be based on the customers goals and the analysis of network assets and risks. A security plan should reference the network topology and include a list of network services that will be provided for example, FTP, web, email, and so on. This list should specify who provides the services, who has access to the services, how access is provided, and who administers the services. As the network designer, you can help the customer evaluate which services are definitely needed, based on the customers business and technical goals.